Source: National Cyber Security – Produced By Gregory Evans
Image via Eduardo Cano Photo Co.
Only three of the world’s Top 100 international airports pass basic security checks, according to a report published last week by cyber-security firm ImmuniWeb.
The three are the Amsterdam Schiphol Airport in the Netherlands, the Helsinki Vantaa Airport in Finland, and the Dublin International Airport in Ireland.
According to ImmuniWeb, these three “may serve a laudable example not just to the aviation industry but to all other industries as well.”
The three are the only airports that passed a long list of security tests that involved checks of their public websites, official mobile applications, and searches for leaks of sensitive airport or passenger data in places like cloud services, public code repositories, or the dark web.
To be more specific, ImmuniWeb scanned for:
- Proper implementation of HTTPS
- If the airport’s email server supports SPF, DKIM and DMARC
- If website content management systems (CMSs) were running up to date versions or vulnerable components
- Compliance tests with PCI DSS, NIST, and HIPAA guidance
- If the airport systems used a web aplication firewall (WAF)
- Tests for common misconfiguration in cookie, header, and other security settings
- If mobile apps used components vulnerable to known exploits
- If mobile apps relied on thirdparty software libraries and frameworks
- If mobile apps employed basic app security settings or if they used unsafe coding techniques
- If airport-related data was available on public cloud storage services
- If airport-related data was available on public code hosting repositories
- If airport-related data was available on the dark web and other criminal and hacking-related websites
The company’s broad suite of security scans revealed that 97% of the tested airports had problems with their cyber-security posture, and primarily with their public websites.
A summary of the company’s scans is available below:
Main Website Security:
- 97% of the websites contain outdated web software
- 24% of the websites contain known and exploitable vulnerabilities
- 76% and 73% of the websites are not compliant with GDPR and PCI DSS respectively
- 24% of the websites have no SSL encryption or use obsolete SSLv3
- 55% of the websites are protected by a WAF
Mobile Application Security:
- 100% of the mobile apps contain at least 5 external software frameworks
- 100% of the mobile apps contain at least 2 vulnerabilities
- 15 security or privacy issues are detected per app on average
- 33.7% of the mobile apps outgoing traffic has no encryption
Dark Web Exposure, Code Repositories and Cloud:
- 66% of the airports are exposed on the Dark Web
- 72 out of 325 exposures are of a critical or high risk indicating a serious breach
- 87% of the airports have data leaks on public code repositories
- 503 out of 3184 leaks are of a critical or high risk potentially enabling a breach
- 3% of the airports have unprotected public cloud with sensitive data

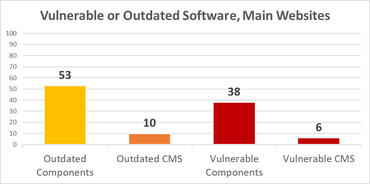
Image via ImmuniWeb
The issues listed above could be credibly exploited to attack an airport authority, obtain a foothold on vulnerable systems, and then infiltrate an airport’s internal network.
Such attacks have happened in the past few years. With the exception of one case — the attack on the Boryspil Kiev international airport — most of these publicly disclosed cyber-attacks have not been deemed dangerous to passenger safety, as attackers were focused on financial gain (by installing malware) or political messages (via website defacements).
However, in a world where nation-state actors are becoming more brazen and political tensions are growing to new heights every day, cyber-attacks against airport systems are not an unimaginable scenario anymore, and should be considered a possible response in the case of an escalation between two countries.
For example, “cyberwarfare and other disruptive technologies” were the two cited reasons why the Doomsday Clock was moved to 100 seconds to midnight last month, showing the growing threat and wide-reaching aftermath that cyber-attacks can cause today.
For context, below are past notable cyber-security incidents involving airport systems and authorities (security incidents with individual airlines not counted):
Source link
——————————————————————————————————
The post #deepweb | <p> Only three of the Top 100 international airports pass basic security checks <p> appeared first on National Cyber Security.
