Source: National Cyber Security – Produced By Gregory Evans
Cybercrime
,
Cyberwarfare / Nation-State Attacks
,
Fraud Management & Cybercrime
UK and US Intelligence Agencies Report That Turla Group Seized OilRig APT Assets
A Russian hacking team stole cyberattack tools from Iran and used them against dozens of targets to exfiltrate data, U.K. and U.S. intelligence agencies say.
See Also: Webinar | Beyond Managed Security Services: SOC-as-a-Service for Financial Institutions
On Monday, Britain’s National Cyber Security Center, a unit of Government Communications Headquarters, or GCHQ, and the U.S. National Security Agency released a joint report into the activities of an advanced persistent threat group known as Turla (see: Researchers: Spies Exploit Microsoft Exchange Backdoor).
While attacks against targets in 35 countries initially appeared to be associated with Iranian APT attackers, NCSC says that its investigation revealed that the Iranian attack infrastructure had been coopted and was being used by Turla for espionage purposes.
“Identifying those responsible for attacks can be very difficult, but the weight of evidence points towards the Turla group being behind this campaign,” says Paul Chichester, the NCSC’s director of operations.
The activities of Turla, also known as Waterbug, Venomous Bear, Uroburos or Snake, have long been tracked by security experts, who suspect that the group is Russian speaking and has ties to Russian intelligence (see: Kaspersky: New ‘TajMahal’ APT Malware Enables Espionage).
Turla has been in existence since at least 2014. It has been tied to numerous campaigns targeting Western governments and businesses, among others (see: Swiss Defense Firm Hack Tied to ‘Turla’ Malware).
The NCSC and NSA stopped short of attributing the group or its activities to the Russian government. But security experts say the finding is undoubtedly an intelligence coup.
“GCHQ catching Russian spies camouflaging as Iranian intel and using their gear is basically the digital equivalent of busting a crafty double agent in a third country, embarrassing two adversaries in one go,” says Thomas Rid, a professor of strategic studies at Johns Hopkins University, via Twitter.
OilRig Attack Tools: Neuron and Nautilus
The coopted attack infrastructure and tools appear to have belonged to the Iranian APT group OilRig – also known as APT34, HelixKitten and Crambus – which many security experts believe is backed by the Iranian government. Historically, its target list has focused heavily on the Middle East, although it hit victims across the globe. Tools previously tied to OilRig include Neuron, Nautilus and Snake.
OilRig has been active since at least 2016. In late 2017 and early 2018, the NCSC issued two advisories on the use of Neuron and Nautilus tools. “These tools were observed in use alongside Snake on a number of victims,” the NCSC said, adding that a large cluster of overall victims were located in the Middle East.
“Victims in this region included military establishments, government departments, scientific organizations and universities,” it said. “Some of these victims, but not all, also had a Snake implant present.”
Evidence of the attacks was first reported by Symantec in June, which reported that Waterbug – aka Turla – appeared to have compromised the OilRig infrastructure in January 2018 and used OilRig’s PoisonFrog control panel to deliver malware to at least one target.
“This is the first time Symantec has observed one targeted attack group seemingly hijack and use the infrastructure of another group,” the security firm’s researchers said.
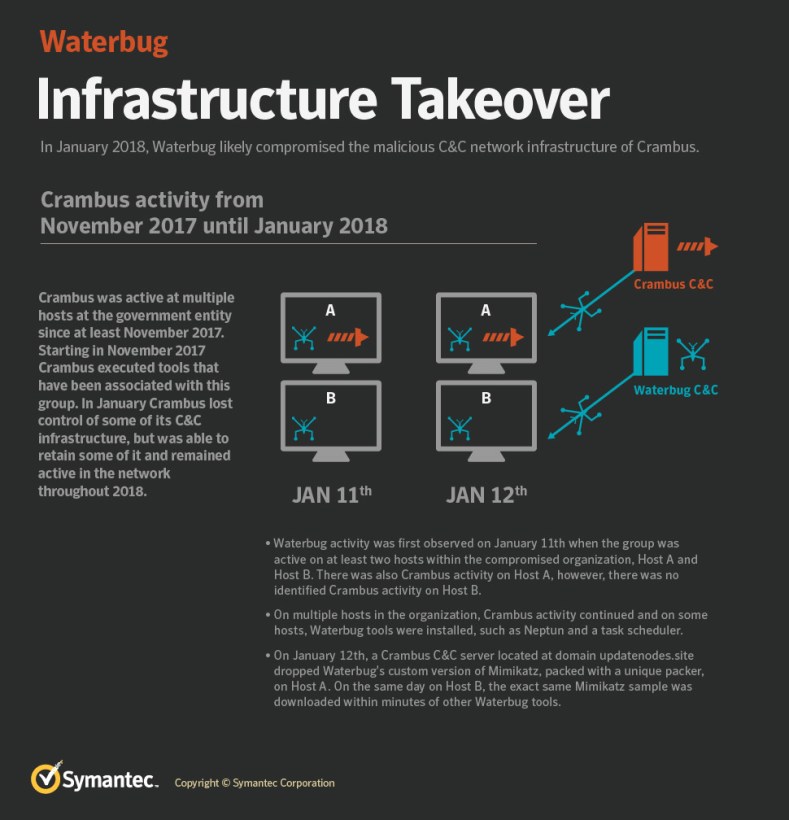
That research was cited by the NCSC and NSA in their joint report. But they stopped short of attributing OilRig attacks to the Iranian government.
Attackers Coopted Attack Infrastructure and Tools
The NCSC says that in some cases, the networks of victims infected with implants associated with Turla had first been infected via virtual private server IP addresses tied to Iranian APT groups, only to later to accessed via a VPS tied to Turla.
The Russian attackers appear to have stolen not just access to the attack infrastructure, but also OilRig’s toolsets, including extensive documentation on implants known as Neuron and Nautilus, given that derivations of those tools were later used by Turla against fresh victims, the intelligence agencies say.
In other words, Russian attackers appear to have extensively compromised OilRig’s operations.
“Data exfiltration from the Iranian infrastructure by Turla included directory listings and files, along with keylogger output containing operational activity from the Iranian actors, including connections to Iranian C2 [command-and-control] domains,” according to the joint report. “This access gave Turla unprecedented insight into the tactics, techniques and procedures (TTPs) of the Iranian APT, including lists of active victims and credentials for accessing their infrastructure, along with the code needed to build versions of tools such as Neuron for use entirely independently of Iranian C2 infrastructure.”
The NCSC says: “In order to initiate connections with the implants, Turla must have had access to relevant cryptographic key material, and likely had access to controller software in order to produce legitimate tasking. Those behind Neuron or Nautilus were almost certainly not aware of, or complicit with, Turla’s use of their implants.”
Among other activities, Turla also scanned existing Snake victims’ networks in at least 35 countries for the presence of an Active Server Page Extended file flaw that could be used to give attackers access to a shell account, the intelligence agencies say. They say one indicator of compromise firms can look for in their security logs are messages that read “!!!MAY BE SHELL!!! (check version)” as well as “!!!MAY BE SHELL!!! (100%).”
“We want to send a clear message that even when cyber actors seek to mask their identity, our capabilities will ultimately identify them,” says the NCSC’s Chichester. “Turla acquired access to Iranian tools and the ability to identify and exploit them to further their own aims.”
Source link
The post #cyberfraud | #cybercriminals | Russian Hackers Coopted Iranian APT Group’s Infrastructure appeared first on National Cyber Security.
