Source: National Cyber Security – Produced By Gregory Evans
Thanks to COVID-19, I am in quarantine after traveling to
Germany. I’m not used to working from home! There are a lot of adjustments I’ve
had to make. The process is giving me a good deal of empathy for the challenges
people and businesses are facing around the globe.
The concept of quarantine because of COVID-19 got me to
thinking about some of the greater implications of this worldwide threat. It
also induced me to consider the ways that the global reaction is a reflection
of the microcosms in which businesses work.
Specifically, watching how the world is adapting and
changing puts me in mind of how these reactions fit into my area of specialty:
cybersecurity. After all, we deal all the time with threats that in many cases
work and operate similarly to a pandemic. People even call them viruses.
The countries showing more success in mitigating the threat
of coronavirus have exercised the same types of activities we in cybersecurity
implement with high determination and effectiveness. In other words, countries
and businesses following both the preventative and reactive steps below are
seeing better results in stopping the threat. Key elements in successful
mitigation include testing for visibility; segmenting or quarantining for
control; and protecting the most vulnerable with good practices.
Test
If you don’t understand the breadth of the problem, you
can’t control it. Testing is key to understanding who has coronavirus, where
they are located, and what other groups of people might be affected as a result
of the initial case.
Figure 1 is a graph of how many COVID-19 tests have been performed per million people,
segmented by country. Figure 2 shows China’s success in combating the virus.
By comparing the two charts, it is clear that China, which
has performed nearly 3,000 tests per million people, is beginning to gain
control of the situation. The COVID-19 tests performed allow the country to
gain visibility into the who, what, when, where, and why of the situation. With
this knowledge in hand, responders can understand the granular details of the
situation, identify new spread areas, and utilize quarantine methods to
mitigate the issue effectively (more on quarantine in a moment).
In other countries, it’s a different situation. For example,
parts of Europe and the United States have done much less testing. As such,
they are beginning to understand that their visibility is very limited. They have
only a small peek into what is going on, and it is commonly believed that the
spread of the virus is much wider in the U.S. than reported.
Similarly, many businesses lack comprehensive visibility
into their systems (their “population”).
When security issues occur, this dearth of clarity makes it
significantly harder to understand the extent of damage done to the business
and how broadly issues might have spread. Testing and visibility into actions,
results, and threats are vital to avoiding widespread compromise, for both
countries and businesses.
Quarantine
The efficacy of quarantine for limiting infection spread has
proved itself time and again. Restricting access to and from infected
populations stops the spread between large areas, whether you are talking about
computer viruses or human ones. The opposite is true as well: The longer it
takes to segment issues, the faster viruses spread. That’s why it’s important
to have a segmented infrastructure in place before issues arise (and, in the
case of COVID-19, quickly get out of control).
China has an infrastructure in place that enables it to
swiftly enforce quarantine rules. More liberal countries have an increased
challenge. There is no philosophical judgment here on which governmental system
is “the best.” However, because of the lack of tight population controls, many
countries have found that the time it takes to put quarantine rules in place
results in a faster spread of the virus.
Furthermore, it becomes difficult to enforce specific
quarantine rules within each area of infected people at risk of being infected
(such as those that were in contact with an infected person). Sadly, countries
that can’t mobilize effectively to enforce this type of targeted quarantine
quickly are paying a very high price.
The same holds true of the digital world: If you don’t have
segmentation rules in place from the get-go, you will have to play catch-up.
Realistically, it’s much harder to attempt to stem issues after they have
already spread across your systems. Moreover, it’s nearly impossible to know
which areas to quarantine if you have little to no visibility into system
activity.
Protect Critical and Vulnerable Assets
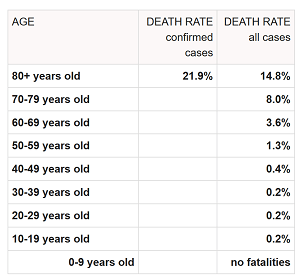
It was clear from the start that COVID-19 was deadlier to
certain demographics, such as those with immunodeficiencies and elderly
citizens. With this in mind, many countries have warned at-risk populations to
avoid travel and stay at home as much as possible. Reducing contact with
potentially infected people is central to protecting important and at-risk
populations (or, in cybersecurity terms, critical and vulnerable assets).
Furthermore, some businesses are splitting their staff (news
anchors, for instance) into separate locations and restricting contact between
them. This reduces the risk of losing critical staff (resources) and negatively
impacting the business. Medical staff and first responders are also much better
protected and cautiously monitored to ensure adequate ongoing vital services.
Similarly, businesses must protect their critical assets,
whether they are applications or people. Ensuring continuity, even in a time of
risk, is central to keeping companies alive and thriving.
Lessons to Consider
While I am in no way minimizing the terrible and frightening
results of COVID-19, there are some clear cybersecurity lessons we can take
from the situation:
1. Gain visibility (aka test) – Your decisions are only as good as the data from your sensors. Visibility during the normal course of business will enable you to manage your assets. Once you are in a crisis (or under attack), visibility brings clarity into what is happening, where it is occurring, and the extent to which the business will be affected. In addition, the ability to answer specific questions can help coordinate your response. For example, for many organizations during NotPetya (targeted ransomware) attacks, it would have been helpful to have a map of all their SMB connections – before they were compromised.
2. Segment (aka quarantine) – Restricting access between segments or areas of your network naturally limits the spread. That’s why segmentation is a good idea during the normal course of business as well as during a crisis. That said, network segmentation can be complicated and hard to implement once you are already under attack. Overlay segmentation solutions may help to achieve segmentation in seconds.
3. Protect (especially vulnerable and critical assets) – Just as we seek to protect the most vulnerable in our society, we must also look to protect digital assets that are the most at risk, including legacy servers, which are likely more vulnerable to attacks. It is also a good idea to secure your critical applications with better protections – for instance by ring-fencing them – than the other parts of your environment. With the right protocols in place, you can ensure they are protected even under the most aggressive attack. Again, this is a good practice to do all the time, but once you are compromised, you need the ability to apply your policies in real time. That’s why it’s important to have measures already in place that can enforce such policies quickly.
4. Control (to reduce impact) – Just like with biological viruses, with computer attacks (especially the wild and aggressive ones) quite often the vulnerability of the propagation method is known. Applying specific controls that target the propagation method help greatly minimize how widely it spreads. COVID-19 is propagating through person-to-person contact. Hence the masks, sanitizers, and no handshake policies. In the business world, for NotPetya attacks, SMBs were the propagation paths, and restricting SMB access to a bare minimum helped reduce the spread. Having the ability to apply whatever type of policy is needed anywhere, and with great speed, provides strong protection for future attacks (which will, realistically, never truly stop coming).
In all honesty, there is nothing new or extraordinary about
these processes. Widely known, healthy best practices are proven to help stop
the spread of coronavirus; the same is true for wide-spreading computer
viruses.
These practices mean that security teams should have
visibility into activities and environments, segment the network to reduce
lateral movement, protect critical assets and vulnerable legacy assets, and
plan these measures by implementing appropriate tools as part of the normal
course of business. That way, during times of crisis, organizations are
prepared to swiftly deploy policies anywhere and keep business safe and running
smoothly.
Original Source link
The post #cybersecurity | hacker | Threat parallels: Coronavirus and cybersecurity appeared first on National Cyber Security.
