Source: National Cyber Security – Produced By Gregory Evans
Image: Nick Abrams/BleepingComputer
A group tracked as Ancient Tortoise is targeting accounts receivable specialists tricking them into sending over aging reports and thus collecting info on customers they can scam in later attack stages.
Aging reports (aka schedule of accounts receivable) are collections of outstanding invoices designed to help a company’s financial department to keep track of customers who haven’t yet paid for goods or services they bought on credit.
These sets of invoices allow accounts and management to get an overview of the company’s credit and collection processes by breaking down the outstanding debts into increments going from thirty to more than ninety days overdue.
Going beyond BEC scams
While BEC aka EAC (short for Email Account Compromise) scammers are known for using social engineering or hacking to switch the bank accounts used by an organization’s financial department to wire out funds, the Ancient Tortoise actors go beyond that.
A report shared exclusively with BleepingComputer that will go live tomorrow shows how researchers at Agari Cyber Intelligence Division (ACID) observed the new threat group impersonating a company’s CFO and requesting an updated aging report together with up to date contact information for each of the customers that had unpaid overdue invoices.
Not asking the company’s employees to change payment accounts is a tactic used by Ancient Tortoise to gain their trust and trick them into following up to their demands for company records.
The attackers also made use of name deception and free email accounts designed to mimic the firm’s CFO to further strengthen their hoax.
However, Agari’s research team was the one who connected with them, continuing the email exchange to further understand the inner workings of Ancient Tortoise’s fraud scheme.
According to Crane Hassold, senior director of threat research at Agari, the research team “happily obliged and sent them a fake aging report containing the names of purported customers, the amounts of overdue payments, and the names and contact details for each of the ‘customers’ accounts payable points of contact.”
The threat actors collected all the fake customer data delivered by Agari’s researchers and, two days after the email exchange, they started contacting all the fake customers, “requesting payment for the outstanding invoices referenced in the aging report” and asking for the outstanding invoices to be paid via ACH or wire to a new account.
To make their email look legitimate, Ancient Tortoise registered a new domain about an hour and a half before sending the messages that closely mimicked our fake employee’s domain. Of course, the display name and username used by the scammer also matched our persona as well. – Agari
Given that the attackers now had all the info they needed to create emails that would perfectly match a supplier’s messages, the damages following a real-world attack were Ancient Tortoise would have legitimate information on their hands could prove to be severe for some of their victims.
This also allows the group to launch attacks that are a lot more convincing (the phishing emails contain info like order numbers, debt amounts, company details) than your run-of-the-mill BEC attack were the threat actors have to rely on their social engineering skills to deceive their targets.
In the next stage of their attack, Ancient Tortoise actors sent details on the bank account they controlled for the outstanding payments to be delivered.
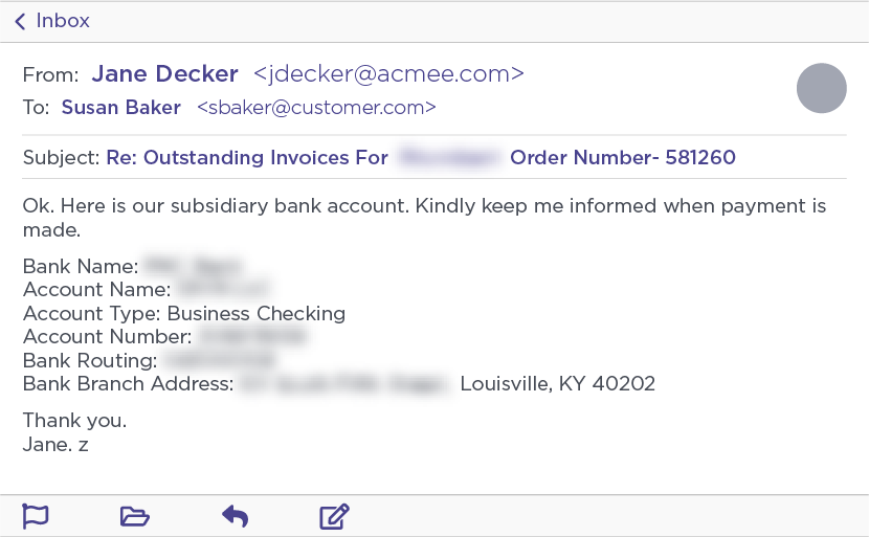
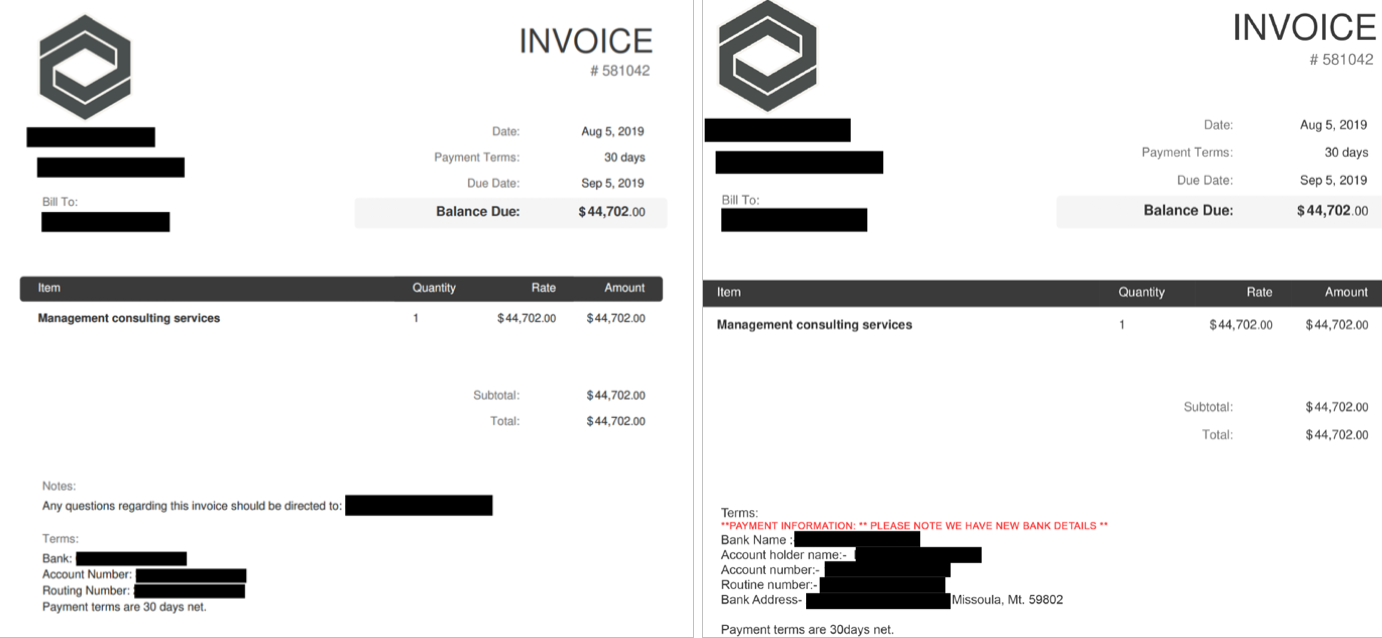
When requested, Ancient Tortoise also sent the fake customers overdue payment invoices altered to show the attackers’ bank account details. This only happened after the actors quickly sent an email to the fake vendor’s employee posing as the CFO to have all outstanding invoices delivered “as soon as possible.”
The BEC scammers delivered the fake within a time span of roughly 45 minutes from the initial request, showing both resourcefulness and speed when it came to making sure that their victims don’t catch on to their scam.
“An analysis of the fake invoice also showed that the scammer’s computer was set to a +4 GMT timezone,” Agari also found. “This information lines up nicely with additional intelligence collected during our engagements that indicates the Ancient Tortoise actor was likely located in Dubai, United Arab Emirates.”
This is just one of the BEC scammer groups Agari is tracking, with others such as Silent Starling, Curious Orca, and Scattered Canary previously being observed running elaborate BEC schemes that led to the compromise of hundreds of employees from hundreds of companies from all over the world.
“In one case, Silent Starling received a consolidated aging report that included details for more than 3,500 customers with past due payments totaling more than $6.5 million,” Agari adds.
When it comes to defense against such attacks, Agari says that “for vendors and suppliers, where the initial malicious email usually impersonates a company executive, a multi-layered approach to email security is essential, which includes implementing strong anti-phishing email and email authentication protections that specialize in defending against advanced identity deception attacks and brand spoofing.
For companies that work with external suppliers, in addition to utilizing identity deception defenses—for aging reports, attackers impersonate vendors rather than executives—having a formal process for handling outgoing payments (especially if supplier’s normal payment account has changed) is one of the best ways to prevent these types of attacks.”
BEC scammers everywhere
According to FBI’s Internet Crime Complaint Center (IC3) Internet Crime report published in April 2019, BEC scams were the cybercrime with the highest reported total losses in 2018, with BEC victims losing over $1,2 billion.
The Financial Crimes Enforcement Network (FinCEN) also released a report in July saying that BEC SAR filings (short for suspicious activity reports) grew from a monthly average of $110 million in 2016 to over $301 million per month in 2018.
The IC3 also issued a PSA in September saying that BEC scams are continuing to grow every year, with a 100% rise in the identified global exposed losses between May 2018 and July 2019, and victim complaints with a total exposed dollar loss of more than $26 billion and related to 166,349 incidents being received between June 2016 and July 2019.
While hard to believe, these figures are somewhat backed by incidents such as the one in which Nikkei, one of the largest media organizations in the world, reported a BEC scam that cost the group roughly $29 million in October.
One month earlier, a member of the Toyota Group also announced that it was scammed in a BEC attack, with an expected financial loss of over $37 million.
Source link
The post #cyberfraud | #cybercriminals | BEC Scammers Use Aging Report Phishing to Find New Targets appeared first on National Cyber Security.
